Configuring the syslog to use TLS streamed over TCP for NSX ALB can only be accomplished through the console because these aren’t exposed via UI. The user interface only allows the specification of UDP. I used self-signed certificates for the AVI controller and AOL, but the process is identical when using CA-signed certificates.
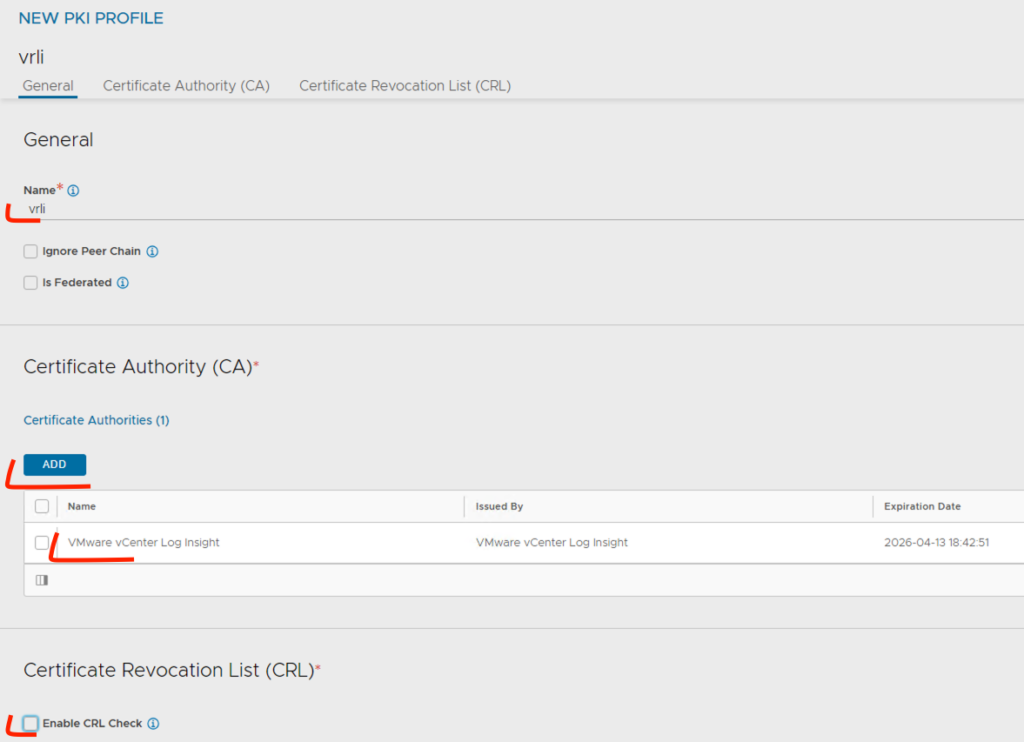
1. Firstly, the certificate for the AVI (controller) needs to be added in the SSL/TLS Certificates. Additionally, the Aria Operations for Logs certificate should be added to a newly created PKI Profile, ensuring that CRL checking is disabled.
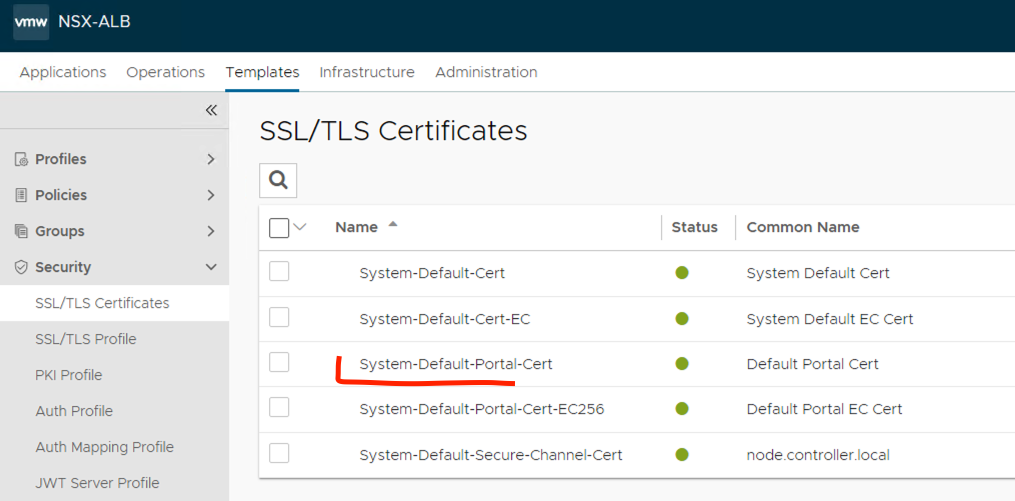
SSL/TLS Profile: go to Templates -> Security-> SSL/TLS Certificates
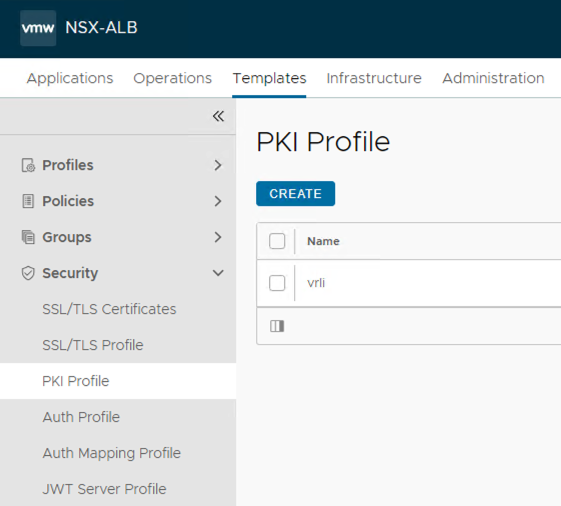
PKI Profile: go to Templates -> Security -> PKI Profile
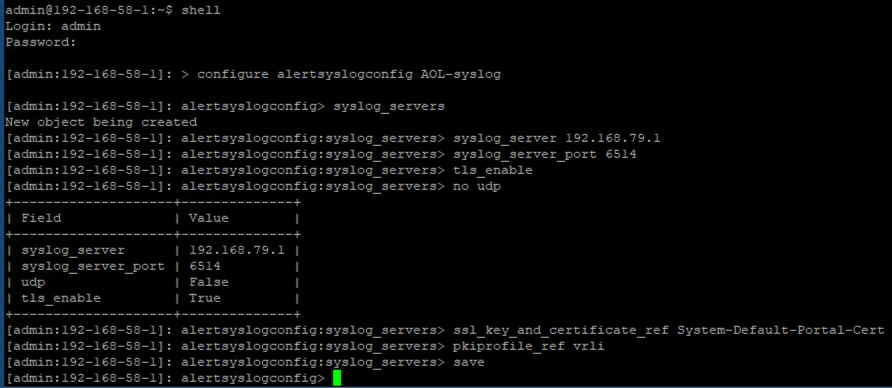
2. Next, SSH into the controller using the admin account. After entering ‘shell’, you will be prompted to input your credentials again and run below commands:
> configure alertsyslogconfig AOL-syslog
alertsyslogconfig> syslog_servers
alertsyslogconfig:syslog_servers> syslog_server 192.168.79.1
alertsyslogconfig:syslog_servers> syslog_server_port 6514
alertsyslogconfig:syslog_servers> tls_enable
alertsyslogconfig:syslog_servers> no udp
alertsyslogconfig:syslog_servers> ssl_key_and_certificate_ref System-Default-Portal-Cert
alertsyslogconfig:syslog_servers> pkiprofile_ref vrli
alertsyslogconfig:syslog_servers> save
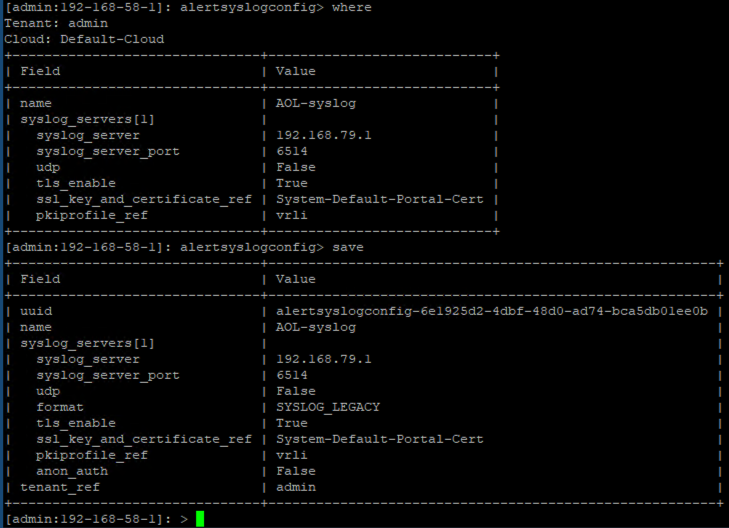
alertsyslogconfig> where
alertsyslogconfig> save
tls_enable – set to true;
no udp – TCP port will be used;
pkiprofile_ref – name of PKI profile created for AOL certificate in step 1;
ssl_key_and_certificate_ref – certificate used for NSX ALB controller selected in step 1;
The syslog should be immediately visible in the NSX ALB UI:
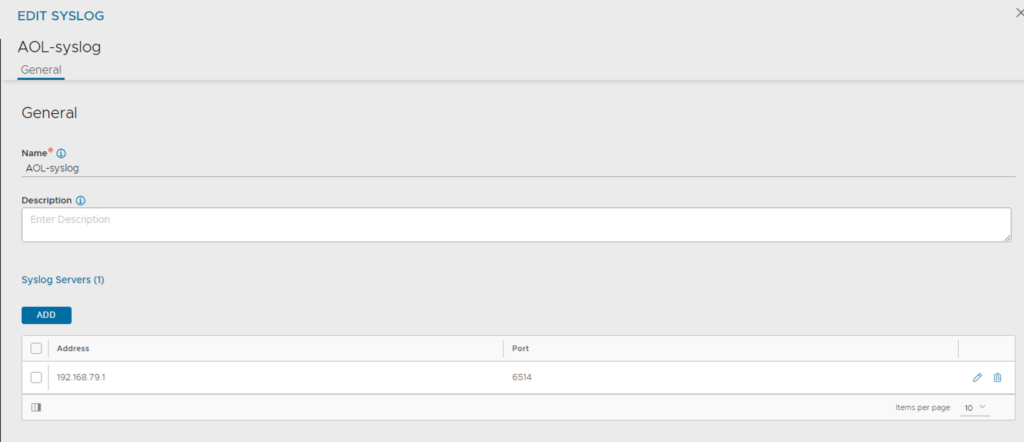
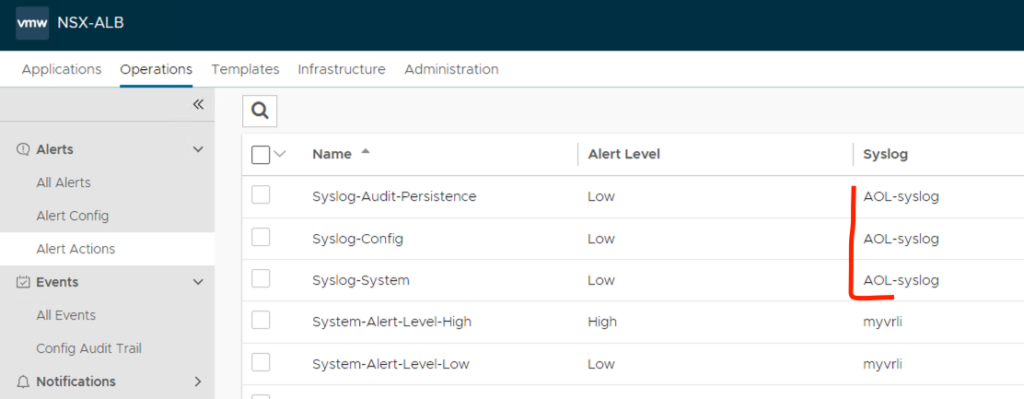
3. Add notification to Alert Actions: go to Operations -> Alerts -> Alert Actions and edit each action, where you wish to include your recently configured syslog server.
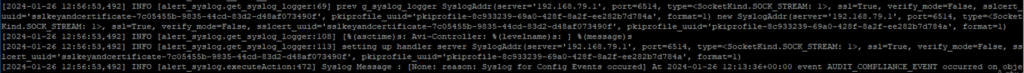
4. To confirm that everything is functioning correctly, you can check the logs at: /var/lib/avi/log/alert_notifications_debug.log
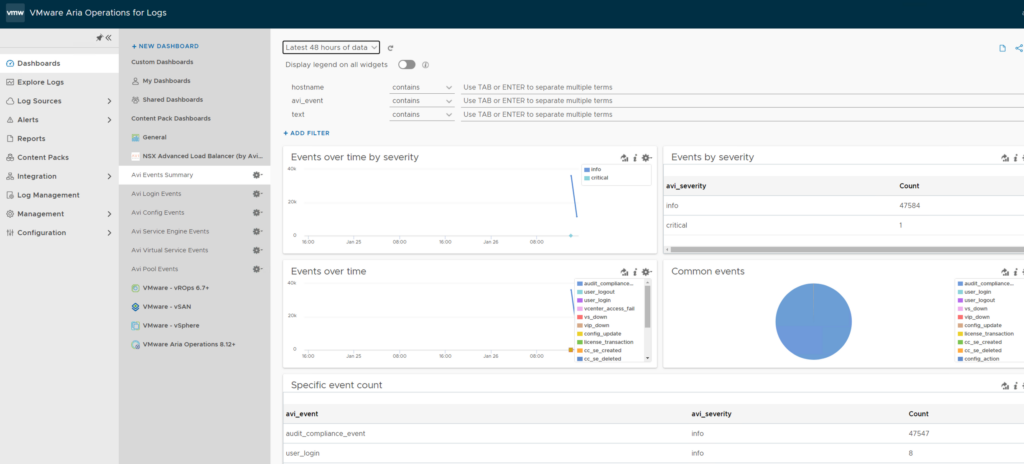
5. View at NSX Advanced Load Balancer dashboards in Aria Operations for Logs: